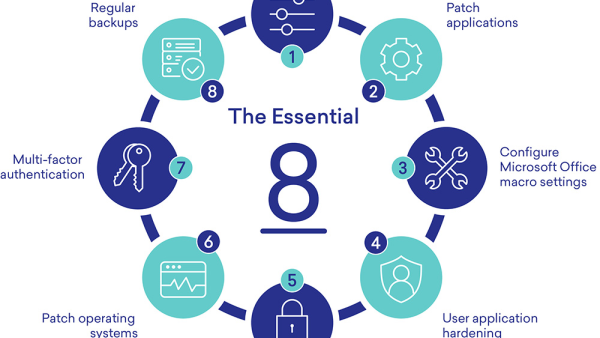
Alternatives to OpenSSL
For more than 20 years, OpenSSL has been the most widely used SSL/TLS library in use by software applications for cryptographic purposes. OpenSSL is free and open source, which is a huge boon for a library serving as the backbone of a secure …